CryptoLocker Ransomware
What is CryptoLocker Ransomware?
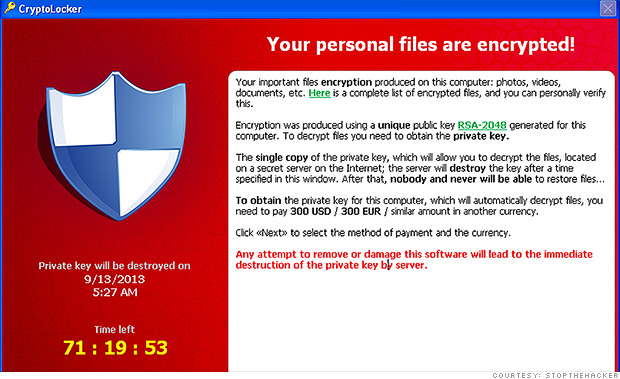
CryptoLocker is a ransomware program that was released around the beginning of September 2013 that targets all versions of Windows including Windows XP, Windows Vista, Windows 7, and Windows 8. This ransomware will encrypt certain files using a mixture of RSA & AES encryption. When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 or $300 in order to decrypt the files, they also asking for Bitcoin for payment because it's difficult to track the source. This screen will also display a timer stating that you have 72 hours, or 4 days, to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted.
Where did this come from?
CryptoLocker appears to have been spreading through fake emails designed to mimic the look of legitimate businesses and through phony FedEx and UPS tracking notices. In addition, there have been reports that some victims saw the malware appear following after a previous infection from one of several botnets frequently leveraged in the cyber-criminal underground.
Victim files are encrypted using asymmetric encryption. Asymmetric encryption uses two different keys for encrypting and decrypting messages. Asymmetric encryption is a more secure form of encryption as only one party is aware of the private key, while both sides know the public key.
The malware has the ability to find and encrypt files located within shared network drives, USB drives, external hard drives, network file shares and even some cloud storage drives. If one computer on a network becomes infected, mapped network drives could also become infected. CryptoLocker then connects to the attackers’ command and control (C2) server to deposit the asymmetric private encryption key out of the victim’s reach. While victims are told they have three days to pay the attacker through a third-party payment method (MoneyPak, Bitcoin), some victims have claimed online that they paid the attackers and did not receive the promised decryption key.
Possible Solution
Prevention
#1 Effective way: Conduct routine backups of important files, keeping the backups stored offline.
Keep your operating system and software up-to-date with the latest patches.
Do not follow unsolicited web links in email. Refer to the Security Tip Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
Use caution when opening email attachments. For more information on safely handling email attachments read Recognizing and Avoiding Email Scams (pdf), and Refer to the Security Tip Using Caution with Email Attachments.
File Restoration
If you had System Restore enabled on the computer, Windows creates shadow copy snapshots that contain copies of your files from that point of time when the system restore snapshot was created. These snapshots may allow us to restore a previous version of our files from before they had been encrypted. This method is not fool proof, though, as even though these files may not be encrypted they also may not be the latest version of the file. Please note that Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, & Windows 8. Save the restored files to an external drive or USB stick.
You can also use a program called Shadow Explorer to restore entire folders at once. When downloading the program, you can either use the full install download or the portable version as both perform the same functionality.
How to find files that have been encrypted by CryptoLocker
Locate encrypted files: ListCriLock
If you wish to generate a list of files that have been encrypted, you can download this tool that I have created:
http://www.computersquad.ca/downloads/ListCrilock.exe
When you run this tool it will generate a log file that contains a list of all encrypted files found under the HKCU\Software\CryptoLocker\Files or the HKCU\Software\CryptoLocker_0388\Files key. Once it has completed it will automatically open this log in Notepad.
Please contact us for additional solutions.
